Your users can sign in to VertiGIS FM via OAuth using their Windows Active Directory credentials. This topic outlines the architecture and required configuration steps.

Windows Authentication Prompt
Architecture
The single sign-on (SSO) architecture for the VertiGIS FM web application and mobile apps vary.
Web Application
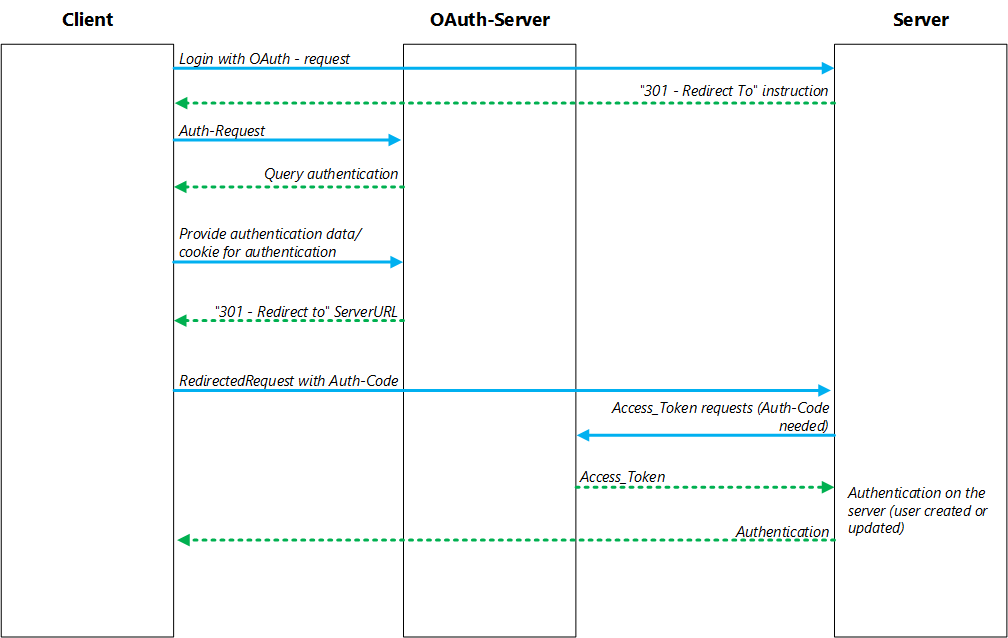
External Authentication Architecture for Web Application
App
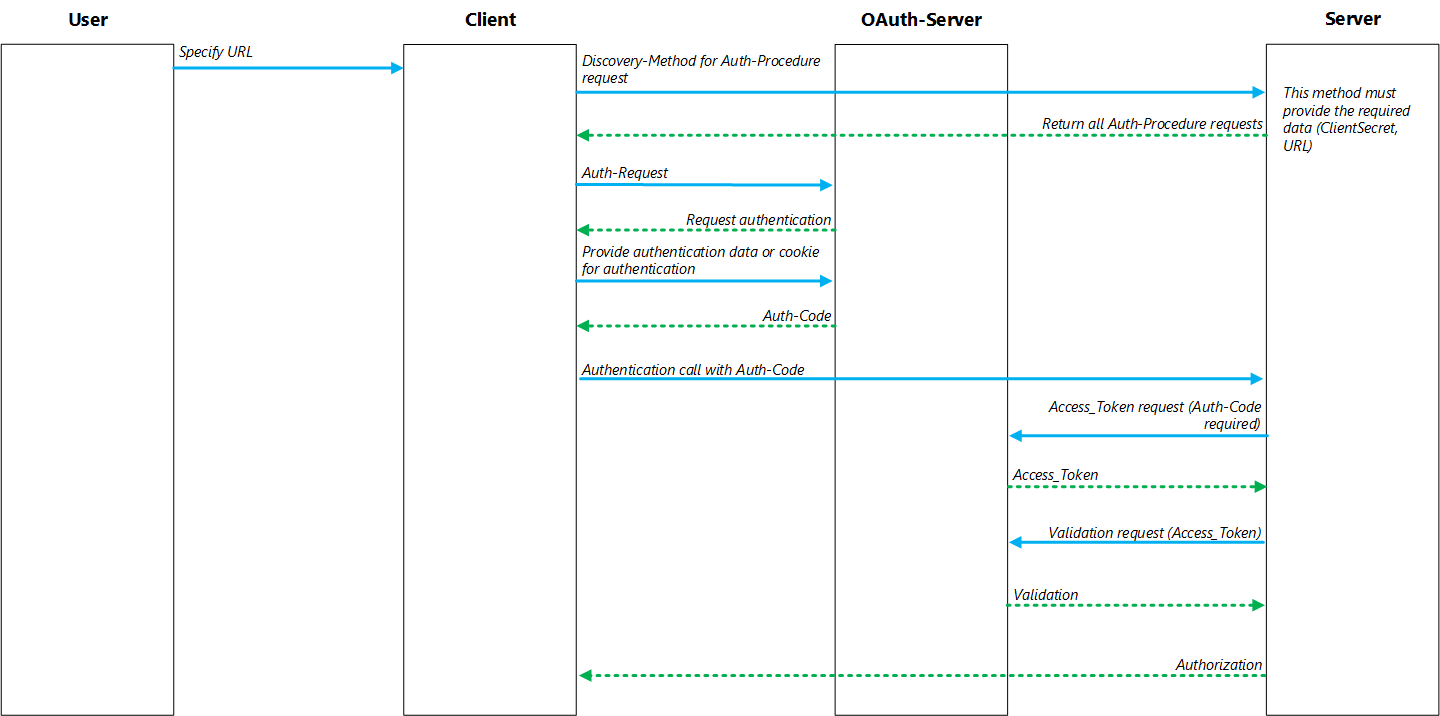
External Authentication Architecture for Mobile App
Register and Configure Microsoft Application for OAuth
To enable OAuth single sign-on in VertiGIS FM, you must register and configure an application in the Microsoft Entra admin center.
You must have an Azure account with an active subscription and Cloud application administrator privileges to complete this procedure.
Register the Application
Begin by navigating to https://entra.microsoft.com/#home and signing in to your account. On the admin center landing page, click Go to Microsoft Entra ID.
Link to Microsoft Entra ID
In the left pane, under Identity, click Applications > App registrations.
App Registrations Link
Click New Registration.
Link to Register New App
You can then enter the name for the application (e.g., VertiGIS FM - OAuth) and select Register an application to integrate with Microsoft Entra ID (App you're developing).
Generic App Name and Integration Selection
In the Name text box, enter a user-facing display name for the application. Under Supported account types, select Accounts in this organization directory only.
Configure the Application for OAuth
Open the Single sign-on tab in the Manage menu. On the Configure appliation properties tile, click Go to application.
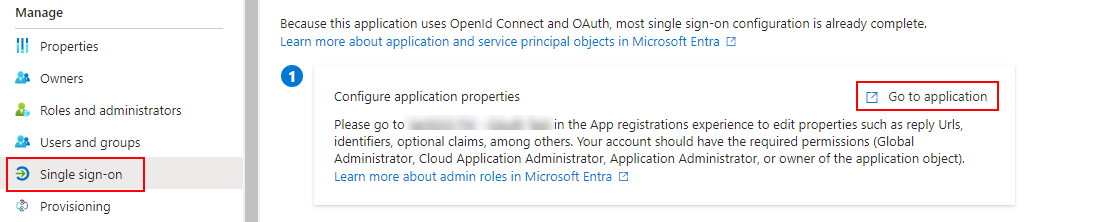
Link to New Application
You can then complete the Authentication, Certificates & secrets, Token Configuration, and API Configuration pieces below. These can be accessed from the new Manage menu that loads.
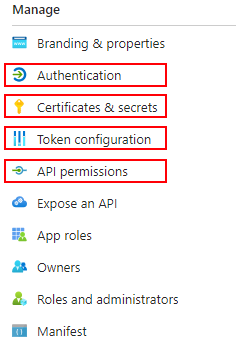
Manage Menu for Registered App
You will also need to complete steps on the Users and Groups tab.
Authentication
In the Authentication tab, click Add a Platform.
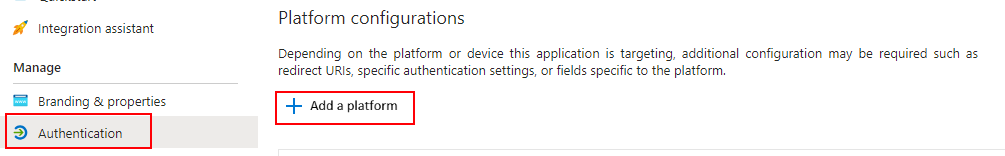
Add a Platform Button for Application Authentication
You need to configure redirect URIs for the web, iOS, and Android platforms. Refer to the table below for required inputs.
Inputs for Redirect URI Configurations
App |
Input(s) |
|---|---|
Web |
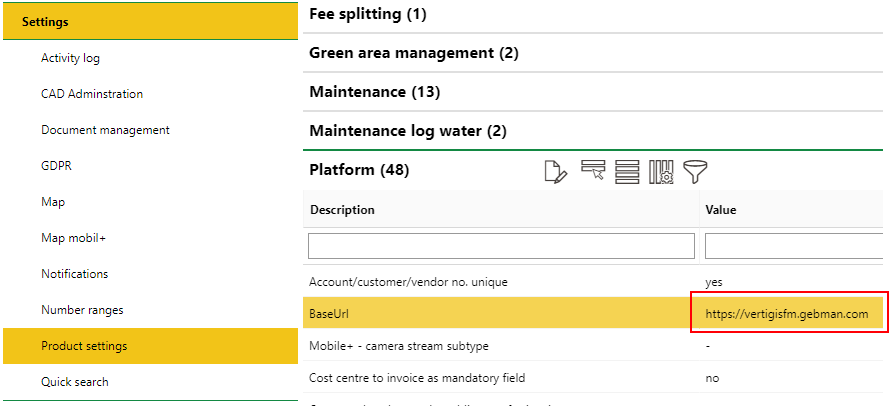
Enter your VertiGIS FM BaseUrl as the redirect URI. The BaseUrl can be found in the Administration > Settings >Product Settings page, in the Platform section.
BaseUrl Value in the Product Settings Click Configure when complete. |
iOS / macOS |
•Bundle ID: com.vertigis.geomanx Click Configure and then Done when complete. |
Android |
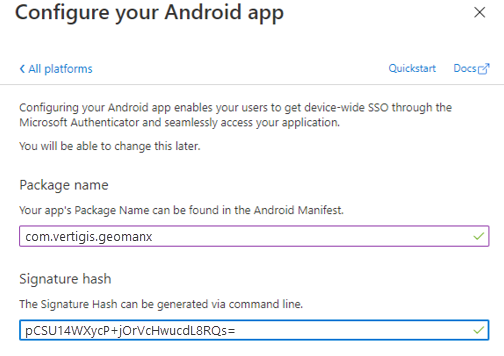
•Package name: com.vertigis.geomanx •Signature hash: pCSU14WXycP+jOrVcHwucdL8RQs=
Package Name and Signature Hash Inputs for Android Click Configure and then Done when complete. |
You will need to enter the redirect URIs generated below when you configure OAuth in VertiGIS FM.
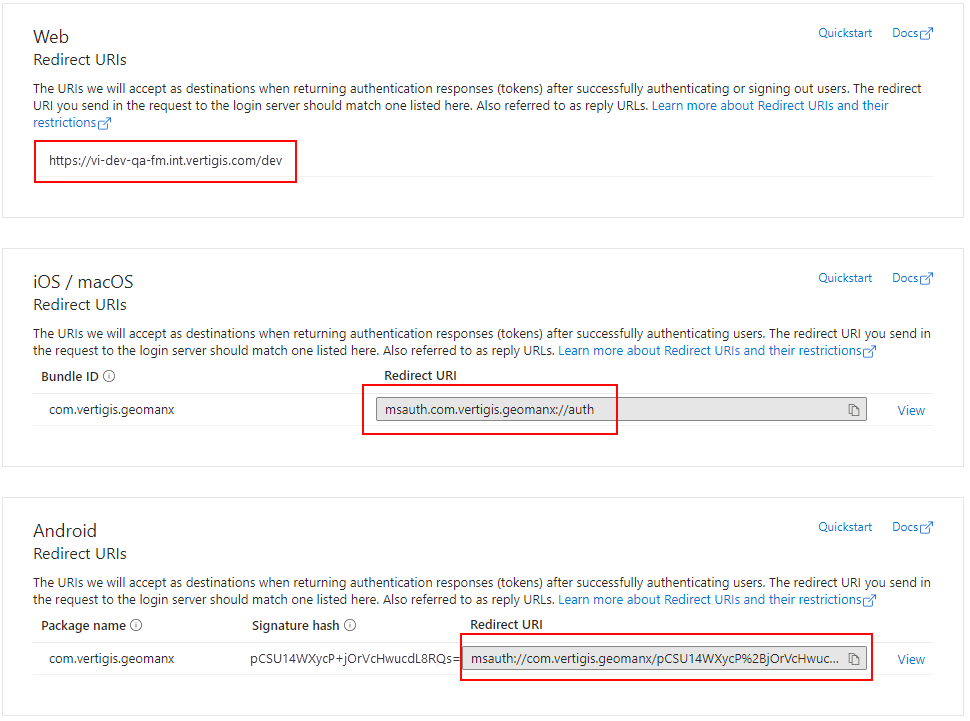
Platform Configuration for Web
Certificates & secrets
In the Certificates & secrets tab, open the Client secrets tab and click New client secret. Enter the string the application uses to prove its identity when requesting a token.
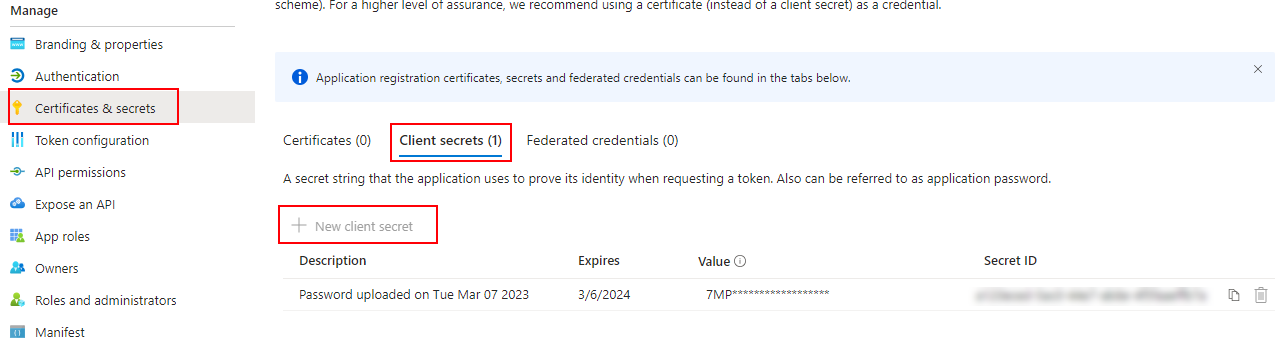
Add Client Secret for Application
Token Configuration
In the Token Configuration tab, click Add optional claim.
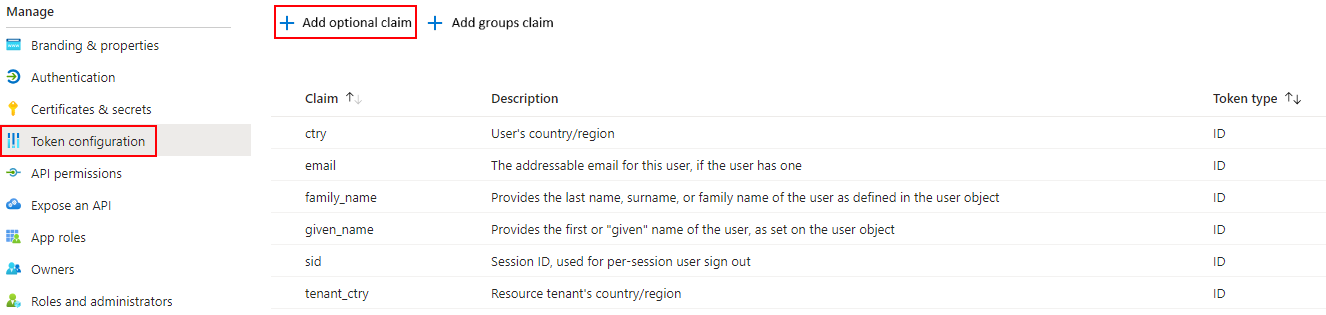
Add Optional Claim Button in the Token Configuration Section
When you add the optional claim, select the Turn on the Microsoft Graph email, profile permission check box.
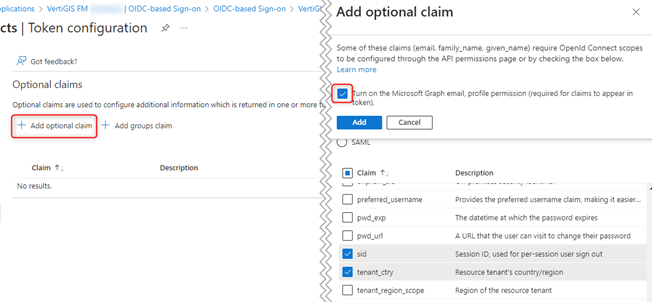
Add Optional Claim
API Permissions
In the API Permissions section, add permissions outlined in the table below under Microsoft Graph.
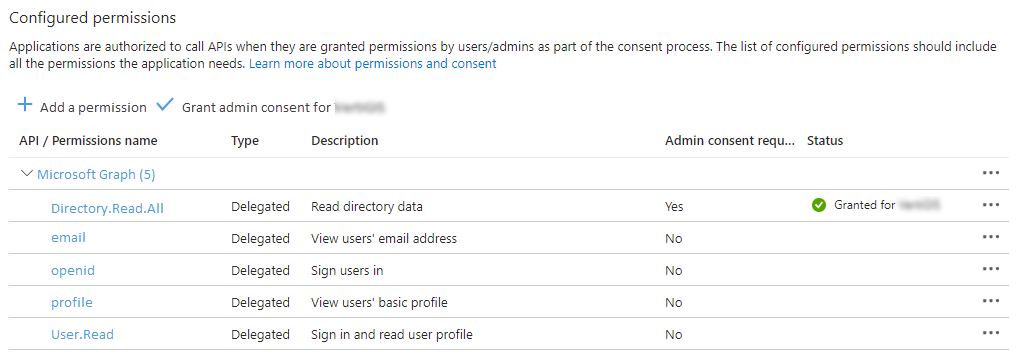
Configured Permissions in API Permissions
API Permissions for OAuth App
Permission |
Admin Consent Required |
|---|---|
Directory.Read.All |
Yes |
No |
|
openid |
No |
profile |
No |
User.Read |
No |
Users and Groups
On the enterprise application page, click Users and Groups.
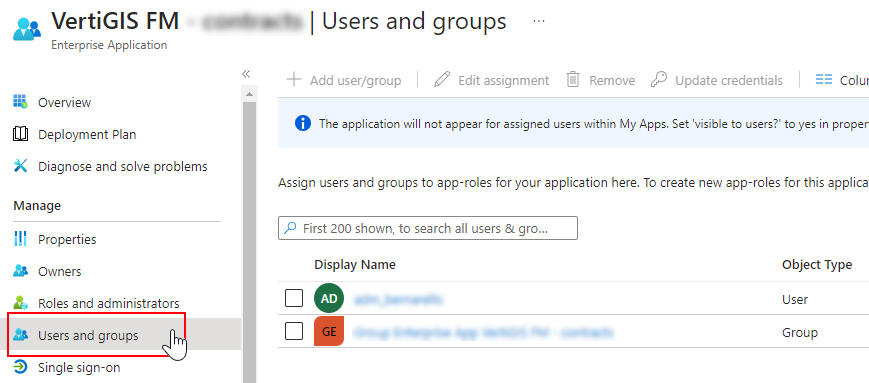
Users and Groups Page
Restrict access to the application by making sure only users or groups you want to be able to access it are added on this page.
Configure OAuth in VertiGIS FM
For your users to authenticate in VertiGIS FM using OAuth, you must also configure OAuth in the external authentication section of VertiGIS FM.
To Configure OAuth
1.In VertiGIS FM, navigate to the Administration > Interfaces > External Authentication page.
2.Click the Add (![]() ) icon.
) icon.
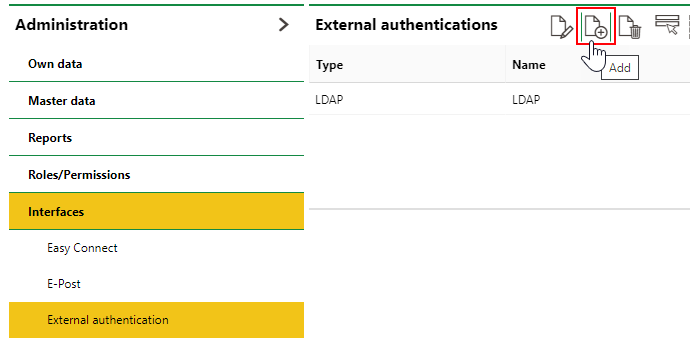
3.Enter the input in the form fields as outlined in the OAuth configuration details.
Inputs for the Reply-Url: Web, Reply-Url: Android, and Reply-Url: iOS fields are generated using the OAuth provider.
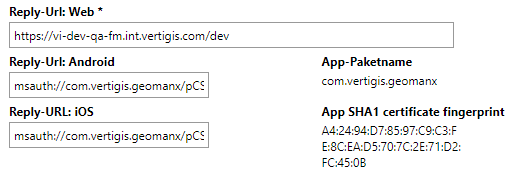
4.Click Save and Close.
Field |
Description |
|---|---|
Reply-Url: Web * |
Enter the base URL of the application here. This value must be entered as the "Reply" or "Response" URL when you set up the authentication point with the OAuth provider. |
Reply-Url: Android and Reply-URL: iOS |
Enter the "Reply" or "Response" URLs generated by the OAuth provider. The App-Paketname and App SHA1 Zertifikatfingerabdruck fields to the right of the Reply-Url: Android and Reply-URL: iOS are used to generate these endpoints. |
DiscoveryUrl * |
Enter the URL specified by the OAuth provider. This URL is used to retrieve the data required for authentication. |
Designation |
Enter a name for the OAuth configuration. |
ClientID * |
Enter the client ID specified by the OAuth provider. This ID is used to identify the OAuth profile. |
ClientSecret * |
Enter the password provided by the OAuth provider. |
TenantId * |
Enter the tenant ID specified by the OAuth provider. |
Scope |
Enter a character string that specifies the fields or authorizations sent to VertiGIS FM from the OAuth provider. The information can vary from provider to provider. |
Web Server Configuration
In Internet Information Services (IIS), you must configure the web to accept query stringers longer than 2048 characters in length. Otherwise, IIS may block responses from authentication servers.
To Configure the Web Server Maximum Query String
1.Open Internet Information Services (IIS).
2.Select the server in the left pane.
3.Under IIS, double-click Request Filtering.
4.Under Actions, click Edit Feature Settings.
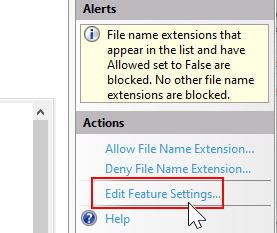
5.In the Maximum Query String (Bytes) box, enter a value of 4096 (or higher).
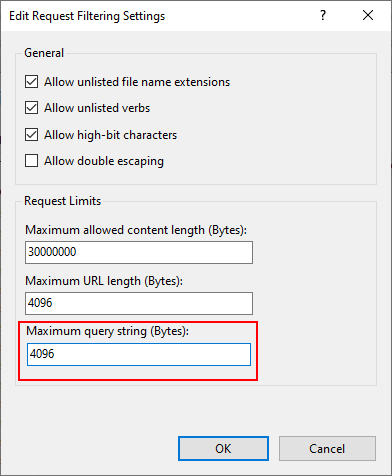
6.Click OK.
You must also ensure the application web host URL is set correctly.
To Ensure the Application Host URL Is Correctly Set
1.Open Internet Information Services (IIS).
2.Right-click the server in the left pane and select Edit Bindings.
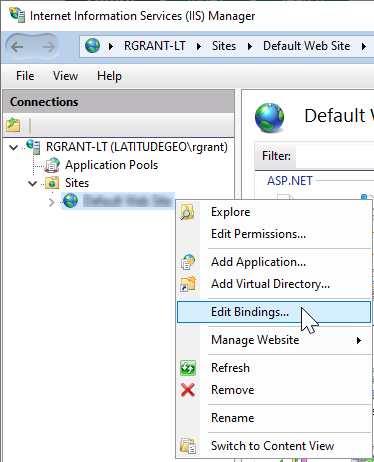
3.Ensure a binding with the settings below exists on the server. You can click Add to add a new binding, or select a binding and click Edit to edit an existing one.
▪Type: https
▪IP Address: *
▪Port: 44368
▪SSL Certificate: Select the certificate retrieved from Microsoft certificate store.
4.Click OK if you added or edited a binding.
5.Click Close.
Log In to VertiGIS FM with OAuth
If your VertiGIS FM environment is configured for single-sign on with OAuth, a Login with OAuth button appears on the VertiGIS FM sign in screen.
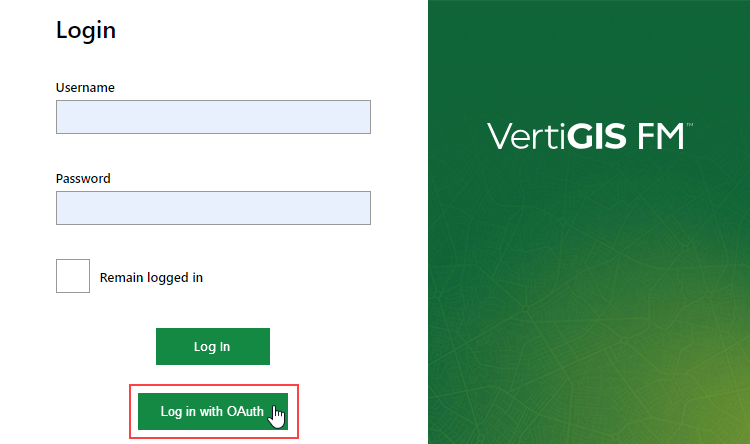
Log in with OAuth Button
If you click Login with OAuth, you will be asked to authenticate with your Windows credentials and then logged into VertiGIS FM automatically.
Refer to OAuth for more information about how to configure your VertiGIS FM implementation for OAuth sign in.
OAuth Log In Parameter
Instead of navigating to the sign page and clicking Login with OAuth, you can add the parameter below to the URL of the sign-in screen for your VertiGIS FM environment. Navigating to this URL bypasses the sign-in screen and takes you directly to the Windows authentication prompt.
__EVENTTARGET=LoginWithOAuth
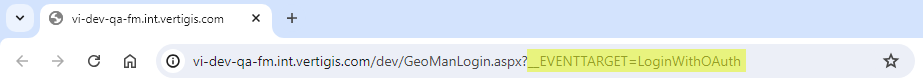
Log In URL with OAuth Parameter
Bookmark the sign-in page URL with this parameter to bypass the sign-in screen when authenticating with OAuth.
Troubleshooting
To debug issues with your OAuth implementation, you can enable verbose logging and review the messages for details regarding data exchanges and possible errors in your system.
To enable verbose OAuth logging, open the log.config file in the Website folder your implementation's installation path. In the <appender> section for the log file, locate the filter entry that contains the <LoggerToMatch value="OAuth.Verbose" /> key-value pair.
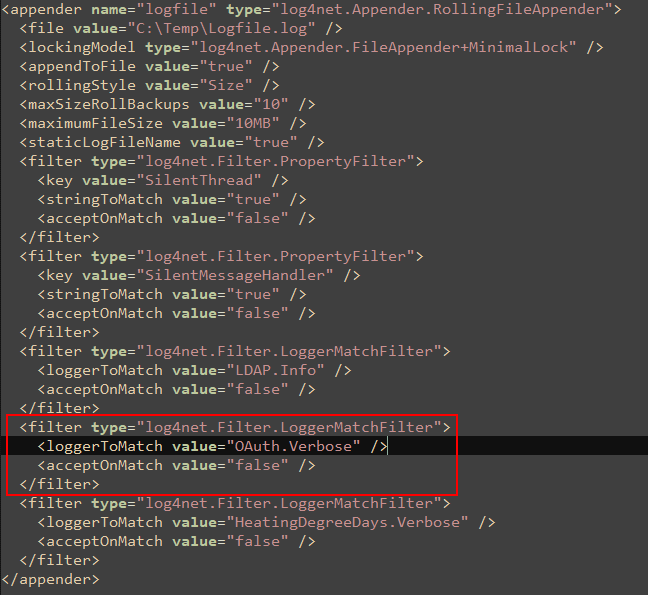
OAuth Verbose Logging Filter Entry
To deactivate the filter and activate verbose logging, it is recommended that you comment out the filter entry above by adding <!-- to the beginning and --> to the end of the section.
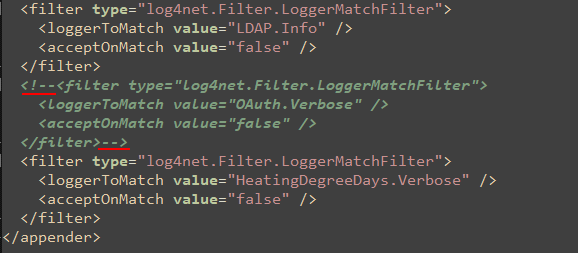
OAuth Verbose Logging Filter Entry Commented Out
Depending on your system and the <appender> section used, you may need to comment out more than one filter containing a <LoggerToMatch value="OAuth.Verbose" /> key-value pair.
Verbose logging will be activated when you save the log.config file after making the changes outlined above. To access the logs, open the file specified in the file value at the top of the <appender> section.
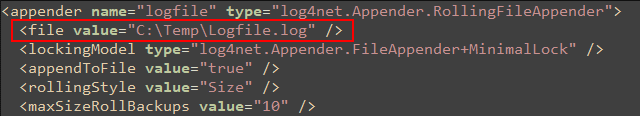
File and Path for Verbose Logging